Bitcoin’s Security Model May Change As Quantum Computing Advances: Analyst

Coinbase’s research director has warned that advances in quantum computing could pose broader risks to Bitcoin than simple wallet theft.
According to David Duong, the global head of the company’s investment research, future quantum machines may be able to break the cryptographic signatures that confirm transactions and may also give miners with quantum power a high speed limit – two different threats that can affect both user funds and the economic model of Bitcoin.
Quantum Risk Goes Off Key
Duong said that about one-third of Bitcoin’s supply can be structurally disclosed because their public keys are already visible on the blockchain. That number is close to 33%, or about 6.51 million BTC, held in address ranges where the public keys are revealed and, in theory, private keys can be found with a sufficiently powerful quantum computer. Reports highlighted that this exposure is mostly from address reuse and old wallet formats.
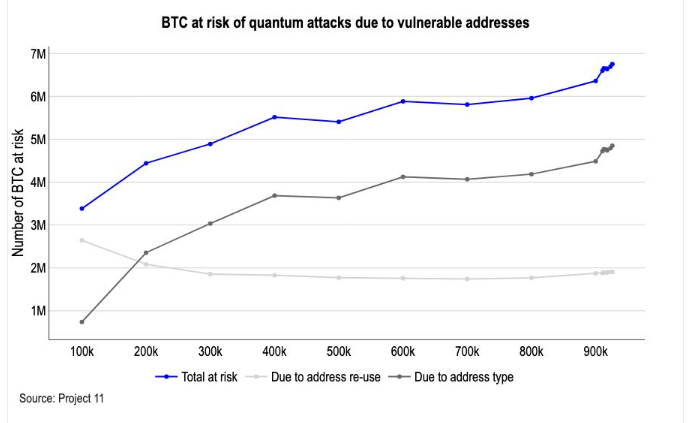
Experts Say There Are Two Main Threats From Technology
Another threat to signatures. Quantum algorithms like Shor, at scale, can convert private keys to public keys, allowing attackers to sign transactions and withdraw funds.
The second is a potential mining problem: a fast enough quantum miner can get proof of work much faster than traditional rigs, annoying incentives and block production. Duong and others emphasize that the signature risk is relatively close in theory, as it only requires cracked signatures tied to exposed public keys.
What the Industry Does
Based on reports, the discussion has already reached fund managers and rating agencies. Some institutional filings have begun flagging quantum vulnerabilities, and NIST and other agencies are pushing work on post-quantum encryption for broader systems.
BTCUSD trading at $92,010 on the 24-hour chart: TradingView
Developers in the crypto space are looking at ways to migrate exchanges to value-resistant schemes, although any such change to Bitcoin would be complex and would require broad agreement.
Long Term Problem, Not Immediate
Duong and other analysts note that today’s quantum machines are too small and noisy to crack Bitcoin’s cryptography. The caveats are about a potential future point often called “Q-day,” when a machine large enough and stable enough to run Shor’s and related algorithms at scale. Time frames vary widely among professionals; some expect decades, others say the gap is narrowing faster than many had predicted.
According to industry sources, coins residing at addresses that already allow for the vulnerability of public keys are the most exposed if a well-designed quantum machine is used. That makes best practices — such as avoiding address reuse and moving old balances to new, value-resistant addresses when they become available — sensible steps. But there is no easy, one-click fix for the entire ecosystem, say experts.
Featured image from Peter Hansen/Getty Images, chart from TradingView

Planning process because bitcoinist focuses on delivering well-researched, accurate, and unbiased content. We maintain strict sourcing standards, and each page is diligently reviewed by our team of senior technical experts and experienced editors. This process ensures the integrity, relevance, and value of our content to our readers.



